Meet the YubiKey, an NFC enabled U2F Zero Trust device that can log you into your PC and online accounts without requiring you to ever enter a password again!
We started with blacklists for applications and services in cybersecurity, but it hasn’t scaled effectively, so we now frequently focus on whitelisting — and where we declare what’s allowed and then block everything else. However, if we take the whitelisting concept to its logical conclusion, we get with Zero Trust infrastructures.
Many systems have a straight-forward definition of trust: untrusted (public), semi-trusted (DMZ), and trusted (private). However, the primary drawback with this approach is that an insider or adversary can frequently situate themselves in the trusted section of the network architecture, so we can’t simply trust entities based on where they are in the network and their levels of access.
As a result, we are moving towards zero trust infrastructures, in which no user, device, or service is trusted at all, and each must prove themselves and be provided only the bare minimum of rights. Whether you like it or not, this is the end goal for cyber security. Along with this, the use of passwords is becoming unworkable, particularly because they create barriers to user access and frequently do not prevent users from falling for phishing emails. Moving to the world of MFA (Multifactor Authentication) and 2FA (Two-factor authentication) is a huge step forwards. These will require the user to provide further verification of their device or themself, such as biometrics, a software token, or other techniques.
FIDO2
The FIDO Alliance and the W3C endorse FIDO2 as a standardised solution to MFA (Multi-factor Authentication) and 2FA (Two-factor Authentication). Most Web browsers already support it, and it attempts to create a password-less authentication solution. According to Lyastani et al [1,] many users feel it acceptable to replace passwords with a security key for authentication. However, there are still concerns about the technology’s use, particularly when it comes to losing the authenticator and getting locked out of accounts. However, these concerns can be easily addressed with simple setups and fail-safe procedures.
Along with client authenticators, FIDO enables the standardisation of second-factor authentication and an integration framework. This standard is known as FIDO2. Each approach employs public-key encryption to protect against risks like as phishing and credential harvesting. As shown in Figure 1, FIDO2 is password-less and supports one or more client authentication methods, including embedded (biometrics and PIN codes) and external (FIDO security keys, wearable devices, and mobile phones).
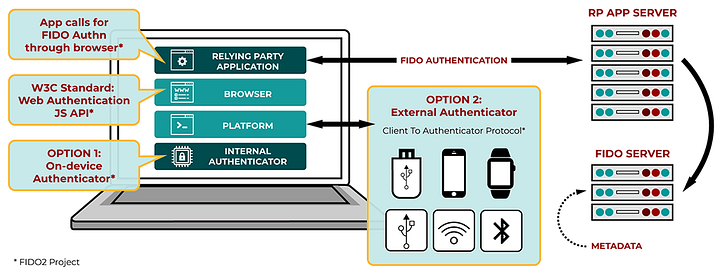
The integration includes:
- W3C WebAuthn. This integrates into compatible browsers.
- CTAP2. This allows for the integration into smartphones using USB, NFC and BLE connections into browsers.
- CTAP1 (previously named U2F — Universal Second Factor). This allows integration with security keys and wearables using USB, NFC and BLE connections into browsers. An example of this is shown in Figure 2.
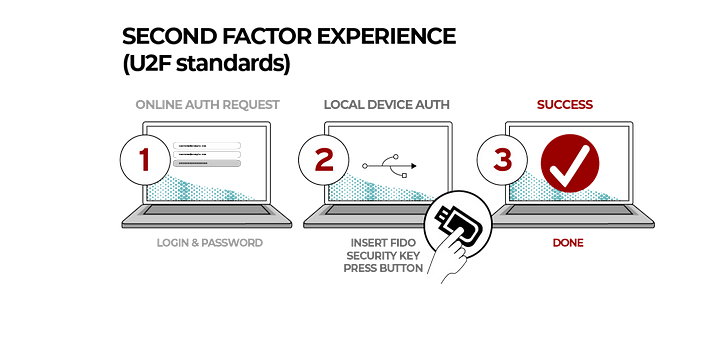
YubiKey
One of the widely used FIDO2 devices for authentication is the YubiKey. Reynolds et al [2] reported on the usage of the YubiKey for Universal 2nd Factor (U2F) security, and where users must press a button on a YubiKey to authenticate themselves. For this they setup the login to Microsoft Windows, Google and Facebook accounts, but reveal problems with the usage of the devices, including lock-outs. These problems often related to the basic setup of the device. Within a second study the researchers found that users generally enjoyed using the YubiKey for daily tasks, and provided advice on improving the setup process. For Arcana, there are generally two ways that their product could use FIDO2 devices. The first is to authentication the device to a service, and the second is to use the device to encrypt the user’s key.
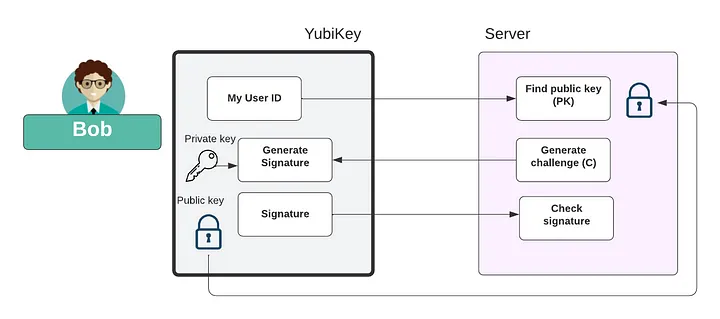
Signing data
Within digital signing, a server (or service) can generate a data challenge and then get the YubiKey to create a digital signature using the private key stored on the device. This signature can then be proven with a public key, and is illustrated in Figure 1. In this way, the server can store the public key of the device, and then match this to a user, when the user want to log into the system, they will need to provide a valid signature that matches their public key.
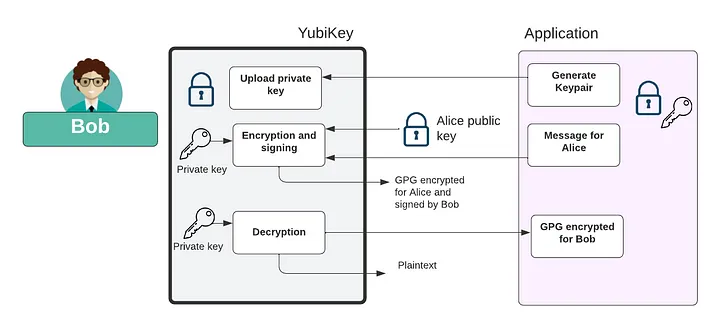
Encrypting data
Along with the YubiKey signing for data with its private key, it is also possible to use it as a method to encrypt and decrypt data. As shown in in Figure 2, we can generate a key pair and then upload the private key onto the YubiKey. This can then be linked to an encryption process. In this case, it is linked to the GPG process, and where we can signing email messages with Bob’s private key, and which will then be proven with Bob’s public key. Along with this we can decrypt ciphered email using the device, and which involves using the private key to decrypt the message.
Conclusions
If you or your company are not moving towards zero trust, ask why not? Zero Trust devices eliminate the need to remember or create strong passwords for your pc and online accounts whilst providing an additional, physical layer of authentication that cannot be replicated by scammers who may be successful in obtaining your usernames or passwords through phishing emails, keylogging or other methods of attack.
References
[1] Lyastani, S. G., Schilling, M., Neumayr, M., Backes, M., & Bugiel, S. (2020, May). Is FIDO2 the Kingslayer of User Authentication? A Comparative Usability Study of FIDO2 Passwordless Authentication. In IEEE Symposium on Security and Privacy (pp. 268–285).
[2] Reynolds, J., Smith, T., Reese, K., Dickinson, L., Ruoti, S., & Seamons, K. (2018, May). A tale of two studies: The best and worst of yubikey usability. In 2018 IEEE Symposium on Security and Privacy (SP) (pp. 872–888). IEEE.
